What is Security Awareness Training (SAT)?
IT and security professionals utilize security awareness training (SAT) as a method to prevent and reduce user risk. These initiatives are intended to educate consumers and workers about their responsibility in preventing data breaches. Employees who undergo effective security awareness training understand good cyber hygiene, the security risks associated with their behaviors, and how to identify potential cyberattacks in email and the web.
The top security awareness training programs use real-world phishing simulations and other web-based communication and reinforcement tools. They ensure users spot cyber threats and methods such as phishing, spear phishing, ransomware, malware, social engineering, and more by working in tandem with educational training courses. In addition, advanced solutions like APT Detection help organizations identify and respond to sophisticated threats that traditional awareness training may not cover.
Aspire's Cybersecurity Certification in New York program helps professionals gain the expertise needed to identify and respond to security risks, contributing to effective security awareness training and enhanced threat management strategies.
Create Your
Human
Firewall
The only behavior-driven security awareness platform that delivers training in real time

Why Aspire Security Awareness Training And Advanced Phishing simulator Tool
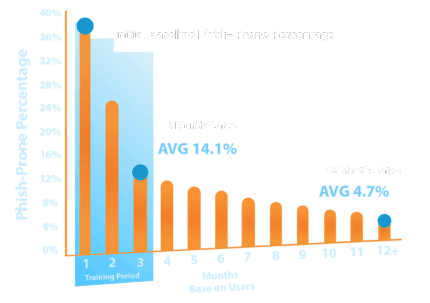
Why Do Your Employees Need Security Awareness Training?
Data breaches stemming from phishing attempts have significantly increased in recent years, and they are now one of the most significant risks confronting commercial, governmental, and charitable organizations. Research indicates that, human error is responsible for more than 90% of security breaches. Security awareness training Security awareness training helps to reduce risk, preventing the loss of personally identifiable information (PII), intellectual property (IP), money, or brand reputation. Employees may make cybersecurity mistakes when using email, the web, and in the physical world, such as tailgating or incorrect document disposal, which can be addressed with an efficient awareness training program.
Many businesses also require security awareness training to comply with industry or regional standards, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Initiative, to name a few (PCI).
When technology fails, your employees need to react
Despite technological advances in email filtering, most CYBERATTACKS still start with malicious emails.
79%
of breaches start with employee’s mistakes
74%
breaches start with phishing and malware
70%
of breaches are due to Social Engineering & Phishing Attacks
30%
of phishing messages get opened by targeted users
90%
of data breaches were caused by human error*
2021 Verizon data breach report
Engaging Security Awareness Training
Aspire's interactive tests and web-based training can be used to determine the users’ level of security knowledge. Educate employees and motivate behavior change through personalized security awareness and training.
To further support ongoing education and awareness, Aspire also offers webinars on key cybersecurity topics, helping employees stay informed about the latest threats and best practices.
Our cloud-based service integrated with our Security Awareness Training, can be installed as a self-managed or managed service. Meet and document compliance, raise awareness with compelling initiatives or automatically give training to personnel who need it the most.
Ready to get started?
Dedicated Training Portal
Each of your employees will have a link to attend online courses at any time using our security awareness training platform. Employee productivity is not disrupted as a result of this. Our training portal is mobile-friendly, allowing users to access it from any device, at any time.
This portal will help the employees develop their cybersecurity knowledge.Employees will be aware of different cyberattacks like phishing, malware, etc., and will gather knowledge on preventing these attacks.Our portal covers every aspect of Cyber Security awareness.That will be the most beneficial part for employees.Since our portal is user- friendly, employees can easily access it from any device.
Real-time Reporting
To discuss progress with stakeholders and validate achievements, track your organization's compliance score, phishing rate, and other metrics.Training is beneficial only when completed on time.Real - time data allows management to quickly analyze the status of staff training.The reports offer real - time information, allowing staff who need to complete training to be reminded.
One of the reasons why real - time data should be incorporated into cyber security is because security experts are trying to keep up with the threats they face.
Ready to get started?
Customize / Create New Courses
Our website is customizable.Is it necessary for you to train your employees in other areas since your employer requires it? Using the platform, you can create new courses or modify existing ones.Fill up the gaps with your inquiries and responses.
Create training materials quickly and easily, then distribute them to your staff.Use a combination of standard and customized training to meet the needs of your staff and company.
We prioritize the safety of our employees.Take this cyber security awareness training to protect your firm from threats such as, malware, ransomware, phishing, and social engineering.Protect your data and networks by preventing unauthorized access.
Enhance Your Security with Comprehensive Toolkits
To empower your employees further and support your security initiatives, Aspire offers comprehensive security awareness toolkits designed to complement our training programs. These toolkits provide practical resources, templates, and guides that help reinforce cybersecurity best practices throughout your organization. By utilizing these toolkits alongside our interactive training and phishing simulations, you can build a stronger human firewall and significantly reduce your risk of data breaches.
Explore our full range of secuurity awareness toolkits to enhance your defense strategy and foster a culture of security vigilance.
Repeat Testing & Continuing Education
According to Verizon, phishing emails are the source of 67 % of all cyber intrusions.You can defend against email - based social engineering assaults and reinforce your most overlooked security asset by using our Phishing Simulation tools.Your staff is on the front lines of the anti - phishing fight, and without them, you can't win. To produce a workforce that is immune to hacker traps, Aspire highly advises a mix of simulated phishing assaults and tailored training.", 'Today, more than ever before, businesses must build a comprehensive security testing plan for their applications, websites, and any other digital product capable of receiving or storing sensitive data from customers, clients, and partners.Additionally, businesses must take proactive actions to protect their brand image on social media, as buyers increasingly utilize these platforms to investigate products before purchasing.Integrating DevSecOps practices into your development cycle ensures that security is a priority from the start, helping to prevent vulnerabilities before they can be exploited.
Secure your remote workforce
If you're looking to increase protection for your organization.
Investigate Business And Financial Misconduct. Evaluate Opportunities and Analyze Risk. Secure Assets And People. Monitor, Remediate And Recover Assets. Respond To And Investigate Data Breaches.








